The COVID-19 pandemic has brought upon an unprecedented time upon global enterprises. In these challenging times, cyber attacks on end-users and organizational infrastructure are at an all-time high. Anup Nair, Executive Director – ITSA & Cyber Security at RSM shares insights on enterprise preparedness against cyber threats lurking in the COVID-19 era
Organizations, in their chase to become global leaders, are ignoring signs and are on the brink of a cyber crime crisis. They can take cognizance of how Trojan horses in the battle of Troy led to its downfall.
With COVID-19, the situation has turned worse due to unprecedented large-scale work-from-home scenarios for enterprises, and that has changed the rules of the engagement.
Every nanosecond there are millions of bytes of data shared across various digital platforms with growing complexities. The nature of this leaves much scope for cyber attacks.
Cyber attacks can potentially disrupt business and can lead to derailment of the company for an hour, a day, a month, a year or forever. Experts predict that by 2021 cyber crimes will cost trillions of dollars.
Technology is like a double-edged sword, which is responsible for optimizing processes with usage of mobility, cloud adoption, digitization, and bringing along with it, security risks that could cost the business everything.
What should organizations do as a way forward?
At the outset, an organization needs to become aware of various cyber security threats. Cyber threat intelligence can help identify security threats for IT teams to ensure cyber criminals are kept at bay. Some of the key security trends noticed in the last few years are as below:
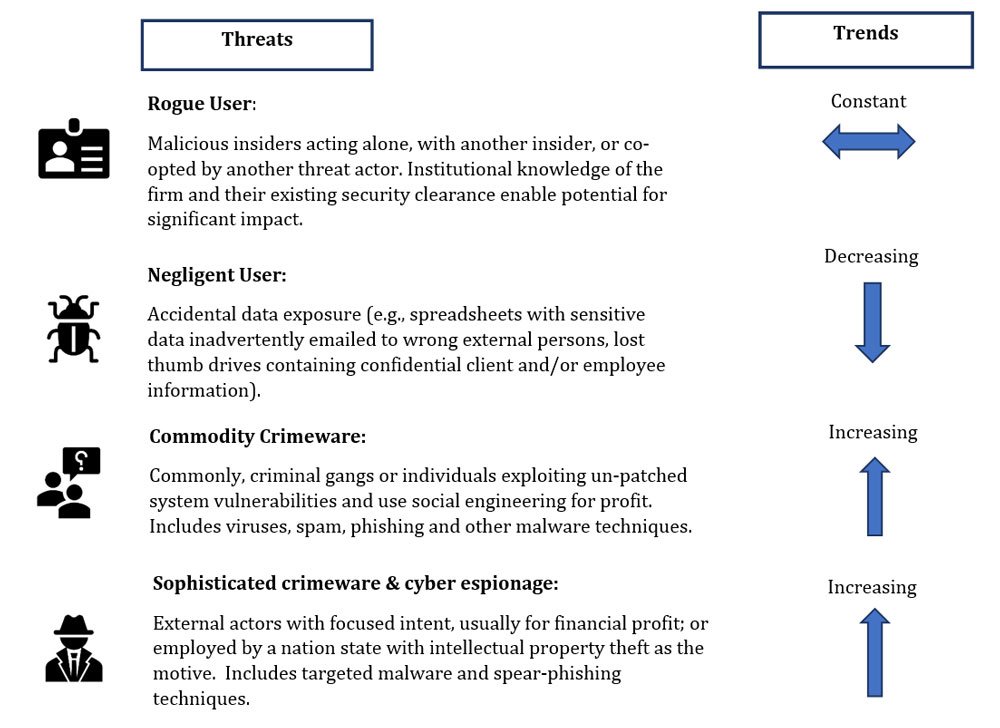
The Scale of Threat
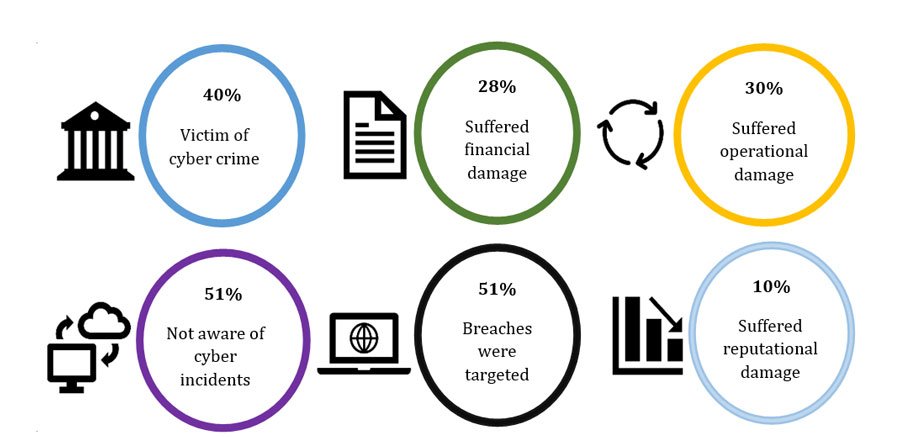
Today, most of the organisations say they have suffered a cyber attack. With Work from Home (WFH) due to COVID-19, becoming the new normal, and with businesses often lacking the proper controls to identify breaches, it is likely that many more have been unknowing victims.
The ramifications are wide-ranging, negatively impacting the businesses’ operations, finances, and reputations. But, many of those that suffered breaches have since done nothing to protect themselves against future attacks. This allows hackers to be aware of organisations’ vulnerabilities and with the change in the work methodologies it makes it easier for them. Methods such as Whaling and Phishing are common ways of attacks. Cyber criminals are scanning networks to find weaknesses.
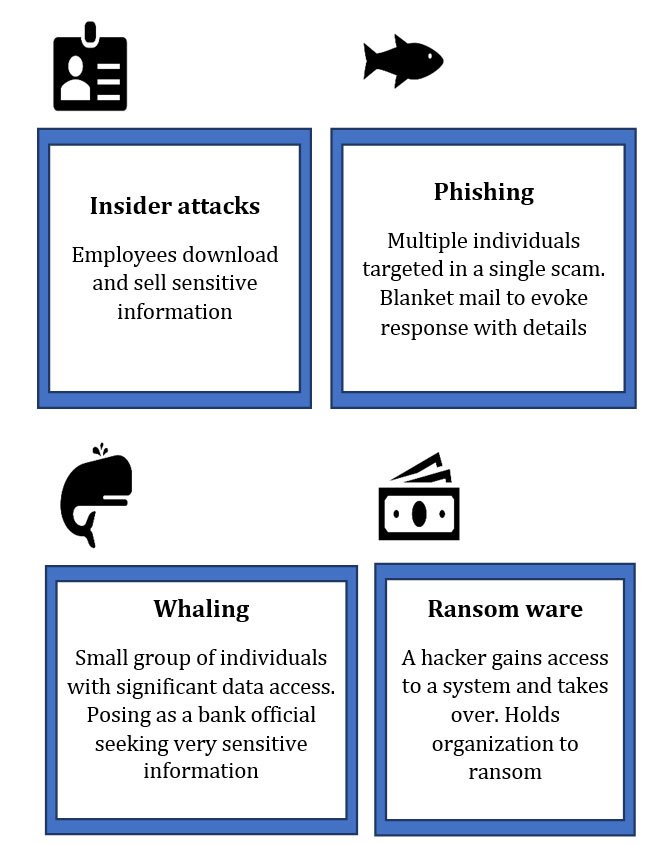
Modus Operandi
There are various ways by which the cyber criminals commit crimes. Employees need to be appropriately trained for these scenarios, so that the same can be avoided as needed.
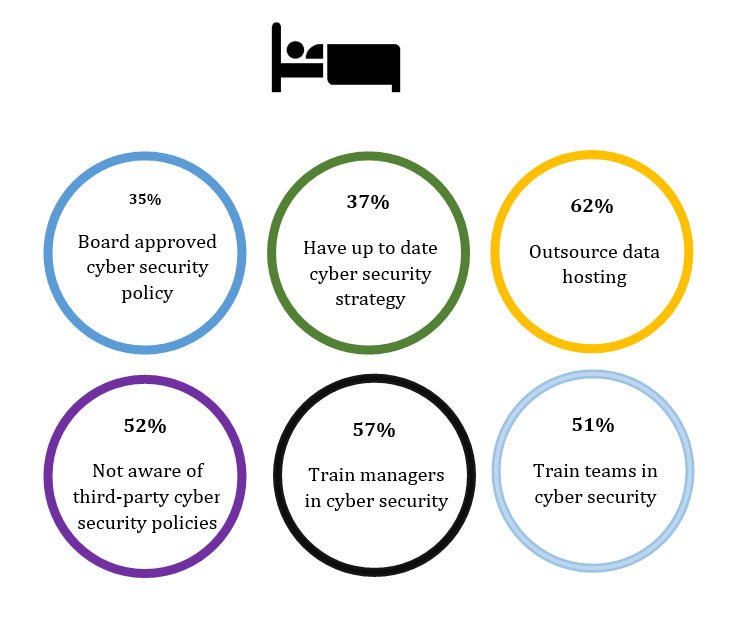
Organizations are caught unaware
Organizations are failing to adhere to core security measures. The DNA for secure practices and actions need to be inculcated organization-wide in employees. Only a few have an up-to date or board-approved cyber security strategy. Security training is often overlooked or falls short of best practice and right checks are missed out by third-party contractors.
How do we protect the Achilles’ Heel?
How can organisations protect themselves against cyber threats? As hacker techniques become more sophisticated, businesses can no longer just rely on technical controls, such as firewalls and gateways. With the COVID-19 scenario the new norm also has affected the way organizations function.
A three-pronged approach can be followed:

Are we future ready?
How can organisations protect themselves against cyber threats? As hacker techniques become more sophisticated, businesses can no longer just rely on technical controls, such as firewalls and gateways. Some areas to look out for are as below:
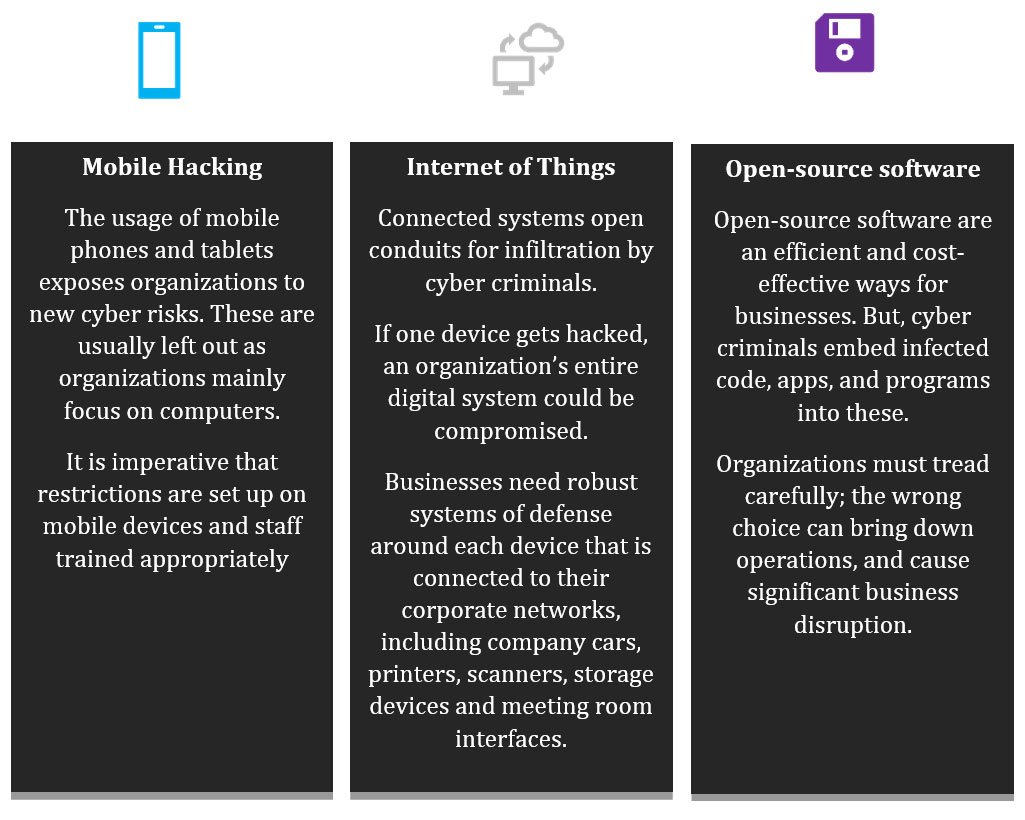
Organizations need to establish a framework to ensure that their cyber security is installed. The following broad framework can be helpful in installing cyber security frameworks at your enterprise.
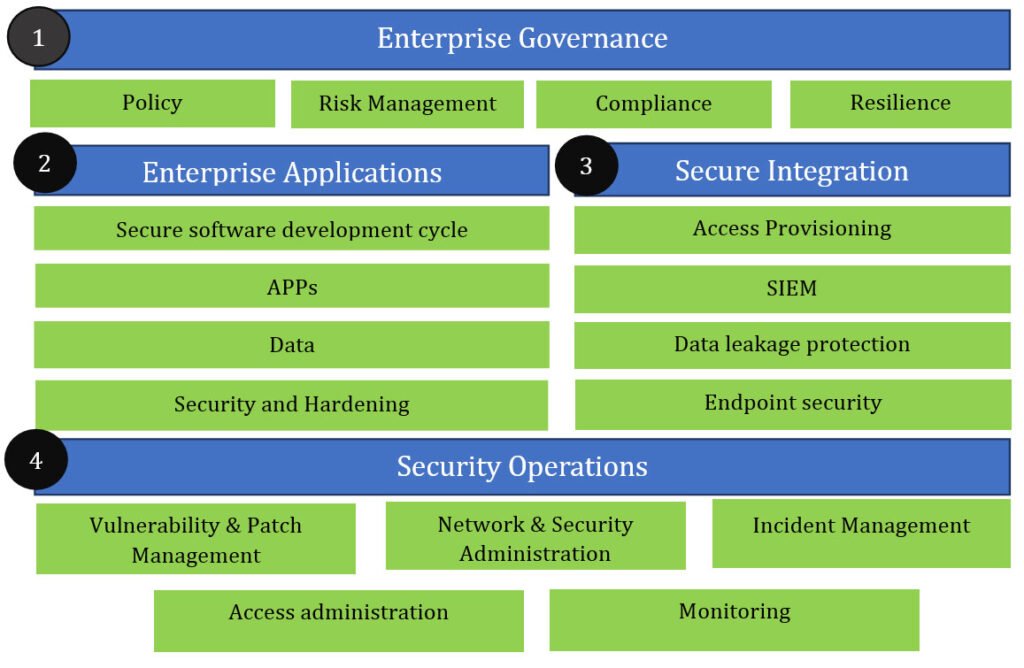
Four Steps to Enterprise Security Preparedness
Based on the above framework, below are the 4 steps that enterprises can take for enhancing cyber threat intelligence and ensuring 360-degree security preparedness for the organization.
1. Enterprise Security Governance
The overarching responsibility of achieving enterprise-wide security can be achieved by following a structured process of setting appropriate Policy, Risk Management framework and ensuring compliance of the same, thereby instilling resilience in the long run.
2. Enterprise Applications and their Secure Configuration & Hardening
Enterprise applications need to be configured appropriately and hardened to ensure that they are not open for cyber attacks.
3. Integrated Security Architecture
The key tenets of Access provisioning, Incident and Event Monitoring, Data Leakage and Endpoint Security in sync with the applications help with a robust environment.
4. Security Operations Center
Have a dedicated team to monitor and tackle all types of security events.

